Hands‑On: Running or Integrating a Distributed Validator
A practical guide for operators and developers. This module covers infrastructure decisions, step-by-step setup using Obol or SSV, operational best practices, and how to integrate DVT into staking platforms using SDKs, APIs, and governance frameworks.
Infrastructure Planning: Bare-Metal vs. Cloud Architectures
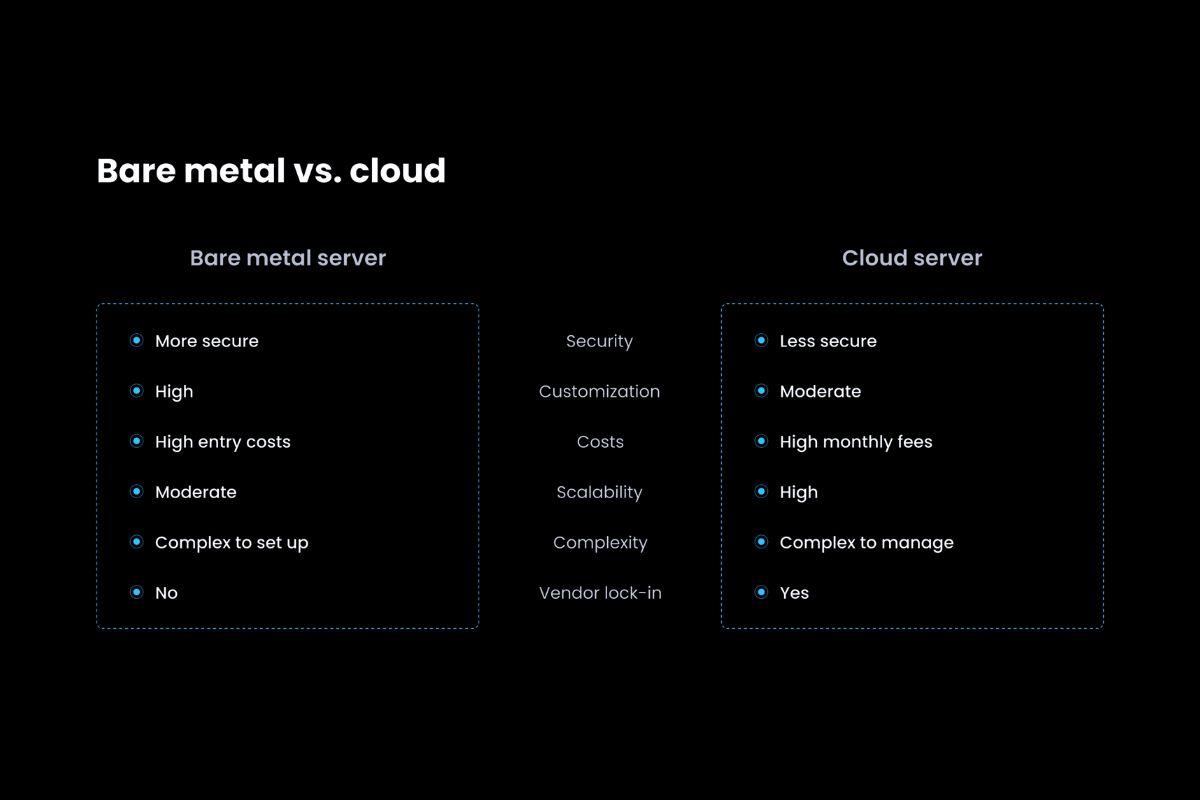
Running a distributed validator cluster begins with infrastructure design. Each node in a DVT setup is an independent participant in a coordinated signing process, which means all nodes must be capable of running Ethereum consensus clients, execution clients, and the DVT coordination layer. The hardware environment—whether cloud-based or bare-metal—has a direct impact on performance, availability, and trust assumptions.
Cloud providers offer elasticity, quick provisioning, and global availability. For small teams or early-stage deployments, using platforms such as AWS, Google Cloud, or Hetzner allows validators to spin up DVT nodes across regions in minutes. However, excessive reliance on centralized cloud infrastructure can introduce correlated failure risk. If a provider experiences downtime or implements policy restrictions, multiple nodes in the same cluster could fail simultaneously, leading to validator inactivity or slashing.
Bare-metal setups, on the other hand, offer stronger control, physical isolation, and reduced dependency on third-party systems. Operators with access to on-premise data centers or regional hosting services may prefer this option to mitigate shared infrastructure risk. However, bare-metal deployments require greater operational overhead, including hardware maintenance, power redundancy, and manual failover systems. In many cases, hybrid setups—with some nodes on cloud and others on bare-metal—offer a balanced architecture that improves both resilience and geographic diversity.
Regardless of environment, network latency and bandwidth are critical. DVT clusters rely on constant inter-node communication for signing duties, so consistent network performance is essential. Operators must monitor latency metrics, minimize jitter, and ensure that their nodes can meet the time-sensitive requirements of Ethereum validator participation windows.
Bootstrapping a DVT Cluster: Obol Charon, SSV Node, or DIY
Once infrastructure is in place, the next step is bootstrapping a validator cluster using a supported DVT implementation. Currently, two production-grade systems exist: Obol Network’s Charon client and SSV.Network’s node software. Both approaches abstract validator duties across multiple nodes using threshold cryptography, but they differ in coordination models and network architecture.
With Obol Charon, operators begin by forming a validator cluster of trusted parties. These operators jointly perform a Distributed Key Generation (DKG) process that produces individual key shares and a public validator key. Each node then runs the Charon middleware, which acts as an intermediary between the validator client (such as Lighthouse or Teku) and the rest of the cluster. Charon handles message relaying, quorum enforcement, and partial signature aggregation. Operators must ensure that each node is correctly configured with the generated key share and can communicate with the others through defined gossip channels. The resulting validator appears to the Ethereum beacon chain as a single entity, despite being operated by multiple independent nodes.
In contrast, SSV.Network introduces a shared public infrastructure layer. Participants can register validator keys on-chain, and the network assigns a set of SSV node operators to manage the validator duties. The key shares are distributed off-chain, but coordination and reputation scoring occur within the SSV protocol. Bootstrapping in this case involves registering as an operator, joining existing validator clusters, or creating new ones using the protocol’s web dashboard or CLI tools. SSV’s design supports operator marketplaces, allowing stakers to delegate validator duties without managing the infrastructure themselves.
For teams with specific security or performance requirements, it is also possible to build custom DVT setups using open cryptographic libraries and MPC frameworks. These DIY clusters require deeper expertise in key sharding, consensus client integration, and signature aggregation, but offer full control over validator logic and network behavior. While not recommended for most users, DIY approaches may be valuable in research, enterprise testing, or protocol-specific validator architectures.
Operational Maintenance: Uptime, Resharding, and Resilience
Once a distributed validator is live, maintaining high uptime becomes the priority. Unlike single-node validators, which can be monitored through local logs and single-point alerts, DVT clusters require multi-node observability. Each node in the cluster must report on liveness, signing participation, and network connectivity. Operators typically deploy metrics exporters, Grafana dashboards, and alerting systems tailored to DVT coordination software to track partial signature contribution and quorum formation in real-time.
If a node goes offline or experiences performance degradation, the validator can continue operating as long as quorum is maintained. However, repeated failures or persistent underperformance by a minority of nodes can erode fault tolerance. Monitoring tools must distinguish between benign downtime and patterns that indicate systemic risk. Operators are encouraged to run health checks on both their validator client and DVT layer, ensuring they receive, process, and relay messages as expected.
Over time, validator key resharding may be necessary. This occurs when operators leave or join a cluster, or when key shares must be rotated for security reasons. In Obol, this requires a re-run of the DKG process with updated participant sets. In SSV.Network, operator rotations can be coordinated through on-chain assignment updates. Key resharding must be handled with care, as incomplete or inconsistent updates can lead to validator inactivity or slashing if quorum thresholds are not met. Backup and restore protocols must be maintained for key share recovery, especially in cases of disk failure or hardware migration.
Another core responsibility is mitigating correlated failures. Operators should proactively diversify across hosting providers, time zones, and client implementations. Ethereum’s consensus diversity principle applies equally in DVT setups: using different consensus clients across nodes reduces the risk that a single software bug will affect the entire cluster. Similarly, spreading nodes across independent DNS providers, firewall rulesets, and operating systems improves overall security posture and ensures that DVT validators are less vulnerable to targeted attacks or infrastructure outages.
Building with DVT: Protocol Integrations and Governance Layers
Beyond validator operation, DVT offers rich possibilities for protocol builders. Staking pools, liquid staking platforms, and modular rollups can integrate DVT as part of their infrastructure to enhance decentralization, availability, and governance coordination.
For staking protocols, integrating DVT begins with technical support for validator registration and key distribution. APIs and SDKs provided by Obol and SSV allow platforms to interface with the DVT coordination layer, automate validator creation, and assign operators to clusters. These tools abstract the complexity of threshold key management and allow staking applications to offer fault-tolerant validators without requiring users to understand cryptographic internals.
In liquid staking environments, DVT introduces a governance dimension. Since validators are operated by multi-party clusters, the selection and rotation of operator sets becomes a governance decision. DAO frameworks can vote on operator admission criteria, performance thresholds, and slashing penalties. DVT thus enables staking protocols to encode decentralization as a protocol feature, rather than relying on off-chain partnerships or static configurations.
Finally, restaking protocols and rollups can extend DVT to non-Ethereum services by using validator clusters for execution, data availability, or fraud proof validation. In such systems, the DVT cluster becomes a programmable coordination layer, where the same quorum logic used for Ethereum signing can be adapted to other security-critical tasks. This composability positions DVT not just as an Ethereum validator enhancement, but as a generalized infrastructure primitive for Web3.





